Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
It was time for me to combine all of my hacking blog updates and statuses so that I’d have one living post!
Starting a hacking blog was always something that I wanted to do. It isn’t the easiest process, but it can be an incredibly rewarding one. If you are considering starting a security blog for your portfolio/resume or knowledge sharing, then do it!
I started my path into hacking blogs with the following, “Hello World” post:
So, I figured it was about time to start a blog to track what I'm currently learning or trying to break. The title of the blog (Security Not Included) comes from a childhood phrase that I think is quite relevant (modified of course) to the realm of Information Security. Back then, the phrase was of course "batteries not included". This is relevant to security as well because users everywhere just expect their systems, applications, and information to be secure out of the box. At the very least, I know I will learn plenty while writing this blog, but I'm hoping someone else does too. (I'll try to keep the blog mostly first-person research and learning, but I may have to slip in some videos or tutorials from time to time.)
This was posted back in May 2013, on a now-defunct Blogger.com site if I’m not mistaken.
I figured that hacking blogging would be a great way to teach others, learn about the field, and improve my career.
I could have never imagined just how far I would have come in the last 8+ years, and I’m so proud of this site and its content.
Get Your NordVPN Offer Now!Well, since I was getting a few updates from WordPress as well as Jetpack, I figured it would be fun to look over a year in my site’s life (plus I could still use some downtime after OSCP).
According to WordPress, my blog received 4,768 views by 2,618 visitors for 1.82 views per visitor over the year.
My most popular posts were the Kioptrix series, which makes sense as Kioptrix is geared more towards beginners.
Surprisingly (to me at least), most of my viewers came from search engines as opposed to VulnHub, which I thought would bring in more.
Most of my outgoing clicks went to PaulSec’s blog, which is all for the explanation on fixing the OpenFuck exploit used in Kioptrix level 1
As I expected, most of my views came from the US, but it was interesting to see where the rest came from (apparently I have a relatively decent following in Indonesia…).
Unfortunately, I am unable to get my Google Webmaster results for the entire year, but they generally leaned towards Kioptrix, errors, and certifications most months (here are my December stats).
The day with the most views (66 in total) was actually on the 22nd of June, but it was fairly easy to figure out why.
This was the day that Filip Ekberg actually tweeted my post about discovering multiple vulnerabilities in his HTTP server.
While it was awesome to see those two events correlate, it showed me that if I want people to read this blog I will need to get it out there and maybe advertise a bit more.
That said, maybe that will come this year in the form of tweets, more public vulnerability findings, conference talks, or guest posts.
All in all, I’m glad I finally picked the blog back up, and I plan on continuing with a post a week for the foreseeable future.
With today being my two-year blogiversary, I thought it would be a good time for another update post!
While my first post was back in May of 2013, I only actually started posting every week back on April 11, 2015, with my eCPPT Review.
This post marks my 104th weekly post, so exactly two years since I started.
First, I had a lot more views (21,518) and visitors (12,805) than in 2016.
That said, this blog is a lot more to me than just sharing content and getting views. It is a way to force myself to learn, and then share that knowledge with as much of the community as possible.
I like to think that I accomplished this in the last year.
I managed to have a few vulnerability disclosures:
There was also a lot of new hardware/toys:
Not to mention, my fairly large tool release:
Kioptrix Level 1 led the year again in views for a specific post, but some of my newer posts (including cert reviews) climbed their way up the ranks.
Most of my clicks still came from Google searches, but a few came from Reddit and Twitter self-promoting.
Paul’s blog on fixing OpenFuck is still the page that gets the most clicks from my site, but I’m glad to see some other stuff up there as well.
My most views in one day took a huge leap, from 66 to 352.
This was mostly because this was the day that I released RWSH and posted about it on a few security sub-Reddits.
That said like I said last year, self-promotion would be the best way to get visitors to my blog.
I saw a lot more views overall this year, and even a little more in 2017.
While this was technically only my 2nd Blogiversary, I’m hoping to have many more, with tons of information to share.
If you’d like to compare to my stats from last year, you can at this post.
Get Your NordVPN Offer Now!With another year in the books, it’s time for my 2017 review!
It is a little earlier in the year than last year, but it’s the holidays and I didn’t want to write a real post.
Some of this information will be the same as my blogiversary post, but that’s because it was also posted this year.
First, I managed to beat my goal of 50,000 views by over 15% this year!
My most popular post this year was my pfSense DNSBL post, which isn’t too surprising. This was a popular topic, and not only among infosec professionals. My Kioptrix walkthrough came in at a solid second, which also makes sense given its introductory nature.
Almost all of my readers are geo-located in the US, but it is fun to see where everyone else’s IP originates from.
My most popular referer by far is still search engine traffic. This is both a blessing and a curse. It is great to get so much organic traffic, but it also means that I could do a better job promoting the site. Additionally, I should probably get better at SEO to increase those numbers more.
Not surprising based on the most popular post, but a lot of my traffic is coming from pfSense searches.
GitHub managed to pass PaulSec’s blog post as my most common outgoing traffic, with a nice mix of my tools + other people’s.
Finally, the most popular time and days for my blog are Monday and 10:00 am respectively. I’m not sure if this is because people are reading my posts once they get into work, or something else. It could be because of the Twitter e-mail updates, an RSS reader program, or another reason entirely.
My most views in a day, for both this year and all-time, was on April 15, 2017.
I managed to get 689 views in one day, which is over 4 times my daily average of 156.
The reason for this spike in viewership was because of a few Reddit posts I made that day. I released my Burp VERBalyzer plugin and shared it with a few different subreddits.
I’d love to get more posts on Reddit, but I don’t want my account used only for shilling my site. I either need to find time to share other things as well or have other people share my posts.
While most of my traffic is still coming organically, my big viewership days are still from some sort of promotion.
I went to, and spoke at, 6 different conferences this year!
I upgraded or picked up some new hardware this year, so I got to do a few write-ups in that category as well. Next year will probably have fewer new toys, but hopefully some more in-depth uses.
With my new job being friendlier towards disclosure, plus more collaboration, I made a lot of new XSS posts. These ranged from various attacks to different filters or limitation avoidance. I still have a few more in the queue for next year, so be on the lookout!
While my tooling wasn’t as active as I would have liked, I still had a few solid releases this year. PyDHCPDiscover and VERBalyzer were entirely new tools that got some decent traction and usage. I also updated RWSH to v1.1, with plenty of ideas for v1.2 or v2.0, which will be coming in 2018!
I even managed to pick up two new eLearnSecurity certifications this year. I’m hoping to finish at least my GXPN and eCRE next year, but we’ll see.
I released a few exploits this year, though most of them were for older vulnerabilities. The two that I’m most proud about are the DB2 one (because I hadn’t seen that specific one before) and the CertReq exfil because I spent a ton of time on it.
I wanted one more category to catch a few other posts that I thought were good this year. The two CTF write-ups are self-explanatory, and I have more coming for 2018. The new job was just something awesome and led to even better quality posts here. Finally, the stealing hashes post was one of the coolest attacks I performed this year, so I had to include it.
First, I plan on continuing my streak of posting (or back-dating) every Saturday next year.
In addition to that, I have set my goal at 70,000+ views for the year.
I got this number based on the last 5 months of this year and extrapolating out.
It should be closer to the 73,000-75,000 range, but I’m not sure if I’ll be able to keep up those numbers yet.
Well, it was a great year for my blog, and I hope you enjoyed it.
Other than more posts, I’m also hoping to try to get some videos started in 2018.
If you have any other ideas, requests, suggestions, or questions, then please send them my way!
Another year down, so it’s 2018 review time!
The timing was great this year, and I got to wait until after the 1st unlike last year.
No blogiversary post this year, but I’m hoping to do something special for my 200th consecutive post!
First, I managed to beat my goal of 70,000 views by over 13%!
For the second year in a row, my most popular post was the pfSense DNSBL post. This is a very popular post and is a very high result in a lot of organic traffic. My second, and my fourth, most popular posts were about new wireless cards and configuration/installation, which also mostly search engine traffic.
An even larger part of my traffic came from the US this year, but I still really like looking at this chart.
My traffic generation was still terrible, and this is a place that I need to focus on next year. That said, it is nice having so many referrals from search engines.
While I cannot grab the search history for my entire year, my wireless card posts drove traffic for the last few months.
Unsurprisingly, GitHub is my most common for outgoing clicks. I’ve thought about adding referral and/or affiliate links for monetization, so this might be an option for 2019.
I still can’t figure out what is causing my most popular day or time, but it is still different from last year’s. While my most popular time is still 10 am, the day changed from Monday to Wednesday.
I was nowhere near my 2017 record of 689 views in one day. This year, my best day was 335 views on September 12th. That said, I made 0 Reddit links to my blog this year. I need to post more on Reddit, as that is where the burst traffic comes from.
That day, it was mostly just generic traffic and views on the eCPPT post, which is always popular.
While this was a miscellaneous category for my post last year, I got through a bunch this year! That said, I still have some that I’d like to finish from years ago, so hopefully, I can get to them.
While I only had two cross-site scripting posts this year, they were still pretty neat. I’ve got some in my draft folder for next year, so I hope to finish those too.
I went to another 6 conferences this year, and again spoke at 3! I don’t have a topic in mind yet, so these numbers may be smaller next year.
I know I posted a lot about x86 this year, but that was due to the SLAE certification. This was a great course, and I learned a ton. I didn’t want to re-link all of my posts, just the most interesting ones here.
This year I managed to knock out another two certifications, which I’m proud of. I haven’t done my SLAE review/exam post yet, so I will just link to the first post I made about it. I plan on getting my OSCE next year, but I am not sure what else yet. I’ve already paid for the eCRE and the eCPTX, but I’m also looking at the pTrace Advanced Software Explotation as an option.
I didn’t release any updates for my most popular tools or release anything novel. That said, if I include this category again, maybe I’ll do better next year!
I had a few other neat posts this year, that I wanted to re-share. The book review was a ton of work, and I’m still really proud of that one.
Based on this year’s statistics, plus my yearly insights, I should probably aim for 80,000 views next year.
That said, I almost hit that this year, so it doesn’t feel like a great goal. I think I will aim for 85,000 views, but I’m willing to adjust this if I spend more time on traffic generation next year.
Other than that, I haven’t missed a post in over three years now, and I don’t plan on starting next year.
This was a great year for my blog, and it kept me slightly motivated during some rougher times.
I also increased my average words per post a lot, which I hope speaks to their quality.
If you have any ideas for more topics, monetization ideas, or ways to branch out, then please let me know! I’ve thought about creating a book(s), courses, consultancies, etc. always bouncing around in my head.
Get Your NordVPN Offer Now!Last year is already over, so here is my 2019 review!
If you haven’t seen my other yearly review posts, this will be similar in style and formatting to those.
I ended up behind a few posts this year due to my break, but I still plan on finishing those up!
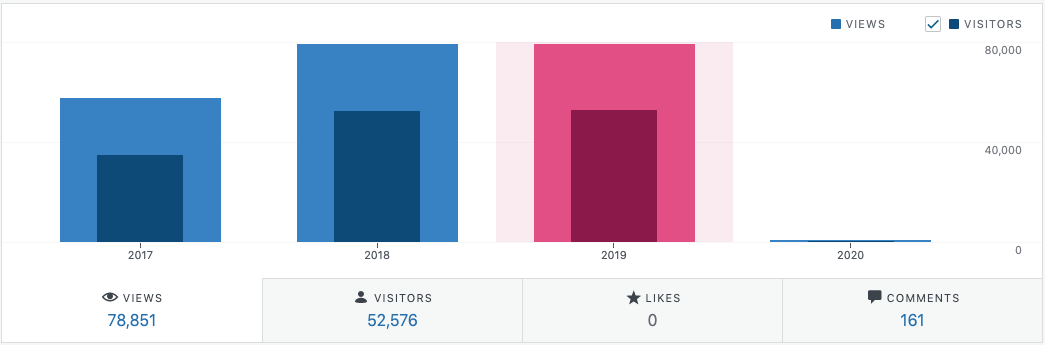
I missed my goal of 85,000 views (as well as last year’s 79,393) by a bit this year, but that’s alright.
This is the third year that my most popular post was the pfSense DNSBL one. This post is mostly organic traffic, which is great. The rest of my top five were still related to wireless cards or attacks, so this is search engine traffic as well.
My US traffic was a bit lower this year, but this is always a fun graphic to look at.
I’m still bad at traffic generation, so I need to improve that in 2020.
I generated a report for my search traffic for all of 2019, which was cool to see. The searches are very similar to last year’s, which is interesting to note.
GitHub is still far and away my biggest outgoing click, but it’s also what I link to the most.
While Wednesday is still my most popular day, the time is now 9 am (instead of midnight).
I finally have a new record for views in one day! On January 20th this year I had 874 views (up from 689 views in a day back in 2017).
There was a lot of traffic on my post from January 19th about a Vulnserver exploit.
I had even more write-ups for CTFs and various challenges this year, so hopefully, they were helpful.
There are also still some from older conferences that I’ve either been holding onto or procrastinating on.
I only attended a few conferences this year, and only spoke at one of them.
I’m hoping to speak some more next year, but I still don’t have a topic in mind yet.
I reported a few vulnerabilities this year and got to release the public disclosures along with the CVE information.
There was also a fun finding that I had on a production system, shortly after someone else’s disclosure.
Cross-site Scripting wasn’t a priority of mine this year, but I still wrote posts for three different filter bypasses.
While it seemed like a slower year, I finished and/or blogged about two new certifications in 2019
I worked on a few vulnserver exploits as well, as preparation for my OSCE as well as fun afterward. I still want to finish every command, so stay on the lookout for those posts.
I also had a few other posts this year that I wanted to re-share.
Based on this year’s stats, plus what happened, I’m going to set my goal back down to 80,000 views for next year.
I also want to finish my goal of 1337+ Twitter followers, which I’m pretty close to already.
This was another great year, and I’m glad that I’ve stuck with this for so long.
I increased my average words per post AGAIN, from 1132 to 1151.
I’m always open for monetization ideas, branching out, or guest posts, so let me know!
I’m a little behind on this post, so my 2020 update isn’t quite ready yet!
Get Your NordVPN Offer Now!I have been running this blog on and off since 2013, with the focus coming and going over the years.
Once I started my weekly posting goal, I got almost THREE HUNDRED posts in a row before taking a longer break.
Now, I still plan on trying to post every week, but the goals are now increased quality (and monetization).
I’d love for feedback on the new site or direction, so hit me up!
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.
[…] he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX,….Read MoreSecurity […]