Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
I’ve been using dnstwist recently, so I figured that I’d share a few examples.
First, if you are not familiar, dnstwist is a domain name permutation engine.
This is great to either find phishing domains, or other types of attacks and impersonations.
For another fitting example, check out my post on homoglyph phishing.
I did not buy a domain for this example, but it would have proved my point even more. That said, this tool has already proven useful on at least one offensive engagement.
Installation was straightforward, and I just ran ‘brew install’ on my Mac.
doyler@mbp:~/tools$ brew install dnstwist Updating Homebrew... ==> Auto-updated Homebrew! Updated 2 taps (homebrew/core and homebrew/cask). ==> New Formulae ... ==> Summary /usr/local/Cellar/[email protected]/3.8.2: 4,124 files, 62.7MB ==> Installing dnstwist ==> Downloading https://homebrew.bintray.com/bottles/dnstwist-20190706_2.mojave.bottle.tar.gz ==> Downloading from https://akamai.bintray.com/bb/bb3daae30fb8252f595a3c109a256a255d5f0bfa6e8d981cd16ccae056314 ######################################################################## 100.0% ==> Pouring dnstwist-20190706_2.mojave.bottle.tar.gz /usr/local/Cellar/dnstwist/20190706_2: 885 files, 10.5MB ==> `brew cleanup` has not been run in 30 days, running now...
First, I ran the tool against this domain.
doyler@mbp:~/tools$ dnstwist doyler.net _ _ _ _ __| |_ __ ___| |___ _(_)___| |_ / _` | '_ \/ __| __\ \ /\ / / / __| __| | (_| | | | \__ \ |_ \ V V /| \__ \ |_ \__,_|_| |_|___/\__| \_/\_/ |_|___/\__| {20190706} Processing 1751 domain variants .............................16%..........................31%................47%......................62%................77%.....................93%..... 12 hits (0%) Original* doyler.net 208.68.36.116 NS:ns-cloud-d1.googledomains.com MX:alt1.gmr-smtp-in.l.google.com Addition doylera.net - Addition doylerb.net - Addition doylerc.net - Addition doylerd.net - Addition doylere.net - Addition doylerf.net - Addition doylerg.net - Addition doylerh.net - Addition doyleri.net - Addition doylerj.net - Addition doylerk.net - ... <snip> ... Bitsquatting doylez.net - Bitsquatting doyleb.net - Bitsquatting doyle2.net 185.230.60.173 Homoglyph doŷleṛ.net - Homoglyph dȯylcr.net - ... <snip> ... Replacement doyper.net - Subdomain d.oyler.net 208.91.197.26 Subdomain do.yler.net - Subdomain doy.ler.net 207.148.248.143 Subdomain doyl.er.net - Subdomain doyle.r.net - Transposition odyler.net - Transposition dyoler.net - Transposition dolyer.net - Transposition doyelr.net - Transposition doylre.net - Vowel-swap dayler.net - Vowel-swap doylir.net - Vowel-swap duyler.net - Vowel-swap doylor.net - Vowel-swap deyler.net - Various doylernet.net - Various doyler-net.com -
As expected, there were no current attacks against me. That said, this did give me a few ideas for future phishing, or other personal domains that I could pick up.
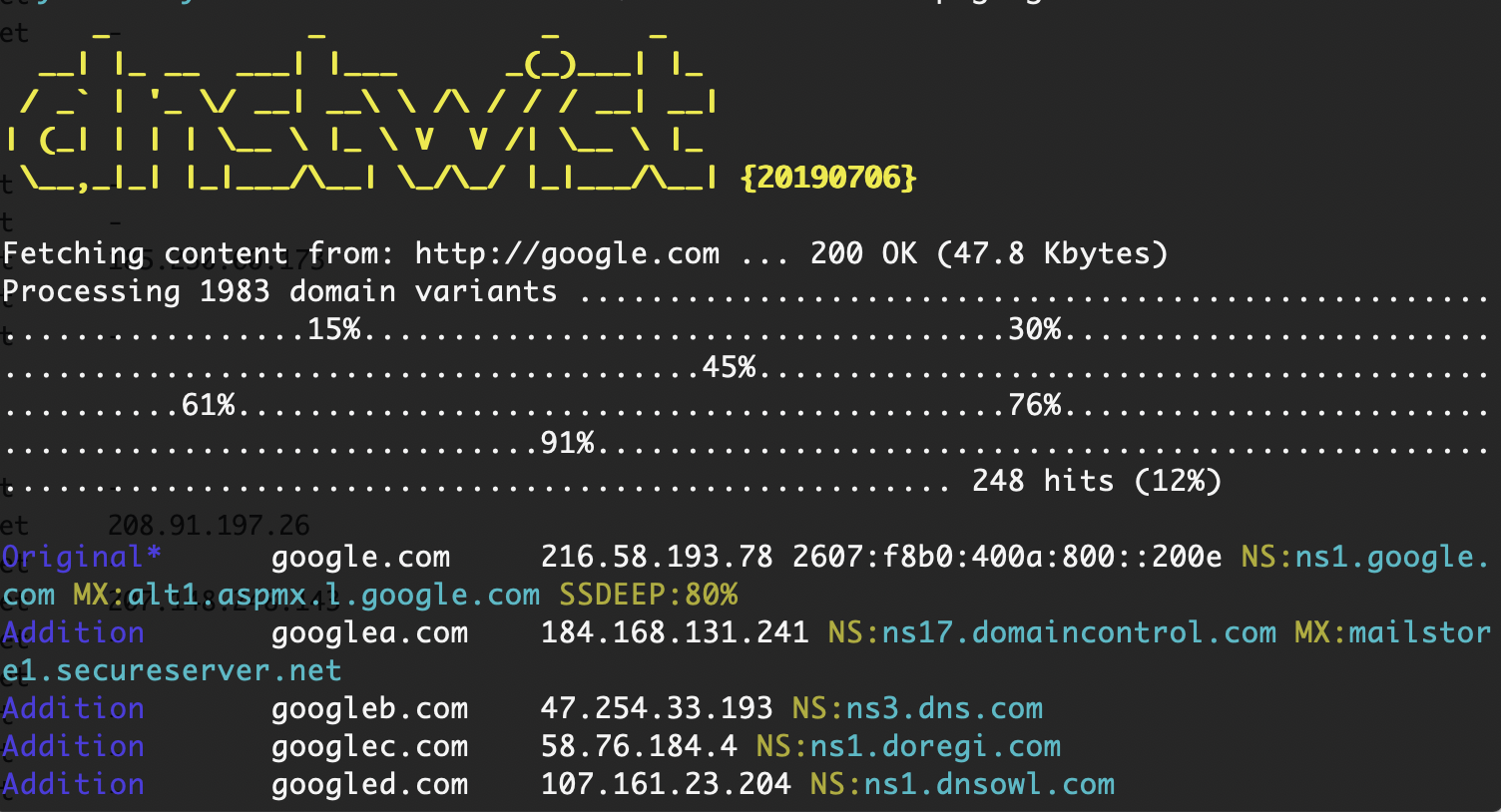
Next, I pointed the tool at Google.
I figured that I might get a few interesting results, and that I would find at least one resource owned by Google or an attacker.
I also used the ‘registered’ flag to not show me any unregistered domains and the ssdeep flag.
doyler@mbp:~/tools$ dnstwist --registered --ssdeep google.com _ _ _ _ __| |_ __ ___| |___ _(_)___| |_ / _` | '_ \/ __| __\ \ /\ / / / __| __| | (_| | | | \__ \ |_ \ V V /| \__ \ |_ \__,_|_| |_|___/\__| \_/\_/ |_|___/\__| {20190706} Fetching content from: http://google.com ... 200 OK (48.4 Kbytes) Processing 1983 domain variants ...........................15%..................31%....................47%.........................62%.............................77%...............93%......................... 239 hits (12%) Original* google.com 172.217.9.206 2607:f8b0:4004:806::200e NS:ns1.google.com MX:alt1.aspmx.l.google.com SSDEEP:79% Addition googlea.com 184.168.131.241 NS:ns17.domaincontrol.com MX:mailstore1.secureserver.net Addition googleb.com 47.254.33.193 NS:ns3.dns.com ... <snip> ... Insertion goolgle.com NS:ns1.google.com Insertion gpoogle.com 104.171.23.69 NS:myns1.fabulous.com SSDEEP:77% Insertion goo0gle.com 54.235.212.68 NS:ns1.pql.net MX:mail.goo0gle.com ... <snip> ... Insertion gioogle.com 207.174.213.34 NS:info267476.earth.orderbox-dns.com Omission googl.com 172.217.15.68 2607:f8b0:4004:810::2004 NS:ns1.google.com MX: SSDEEP:69% Omission gogle.com 172.217.15.68 2607:f8b0:4004:810::2004 NS:ns1.google.com MX: SSDEEP:69% Omission googe.com 162.243.10.151 NS:ns1.yourdoor.com Omission goole.com 217.160.0.201 NS:ns1083.ui-dns.biz MX:mx00.1and1.co.uk Omission oogle.com 104.28.28.162 2606:4700:3032::681c:1ca2 NS:amir.ns.cloudflare.com MX:mx.zoho.com Repetition googlle.com 3.212.82.98 NS:ns3.domainmanager.com MX:mx94.mb1p.com Repetition googgle.com NS:ns1.googledomains.com Repetition ggoogle.com 172.217.13.228 2607:f8b0:4004:809::2004 NS:ns1.google.com MX: Repetition gooogle.com 172.217.15.100 2607:f8b0:4004:811::2004 NS:ns1.google.com MX: SSDEEP:68% Replacement hoogle.com 107.180.25.196 NS:ns41.domaincontrol.com MX:mailstore1.secureserver.net ... <snip> ... Transposition ogogle.com 172.217.164.132 2607:f8b0:4004:814::2004 NS:ns1.google.com MX: Transposition gogole.com 172.217.7.196 2607:f8b0:4004:801::2004 NS:ns1.google.com MX: SSDEEP:69% Transposition goolge.com 172.217.13.228 2607:f8b0:4004:809::2004 NS:ns1.google.com MX: SSDEEP:71% Transposition googel.com 172.217.8.4 2607:f8b0:4004:803::2004 NS:ns1.google.com MX: SSDEEP:69%
As you can see, there were a few interesting results, including a few domains with an SSDEEP score over 60%.
When I went to visit one that a potential actor might use, it was already a redirect to Google!
While I cannot give the exact example that I used during an engagement, I hope that this was a good enough demonstration.
Attackers or defenders can easily use dnstwist, and the usage is very straightforward.
This is a tool that I’ve thought about writing myself, but I might not have to for the time being.
If you have any examples of active phishing domains, then please let me know!
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.